INSUBCONTINENT EXCLUSIVE:
It not been a great week for cell carriers
EE was hit withtwo security bugs and T-Mobile admitted a data breach
Now, Sprint is the latest phone giant to admit a security lapse, TechCrunch has learned.
Using two sets of weak, easy-to-guess usernames and
passwords, a security researcher accessed an internal Sprint staff portal
Because the portal log-in page didn''t use two-factor authentication, the researcher — who did not want to be named — navigated to pages
that could have allowed access customer account data.
Sprint is the fourth largest US cell network with 55 million customers.
TechCrunch
passed on details and screenshots of the issue to Sprint, which confirmed the findings in an email.
After looking into this, we do not
believe customer information can be obtained without successful authentication to the site,& said a Sprint spokesperson.
Based on the
information and screenshots provided, legitimate credentials were utilized to access the site
Regardless, the security of our customers is a top priority, and our team is working diligently to research this issue and immediately
changed the passwords associated with these accounts,& the spokesperson said.
We&re not disclosing the passwords, but suffice to say they
were not difficult to guess.
The first set of credentials let the researcher into a prepaid Sprint employee portal that gave staff access to
Sprint customer data — as well as Boost Mobile and Virgin Mobile, which are Sprint subsidiaries
The researcher used another set of credentials to gain access to a part of the website, which he said gave him access to a portal for
customer account data.
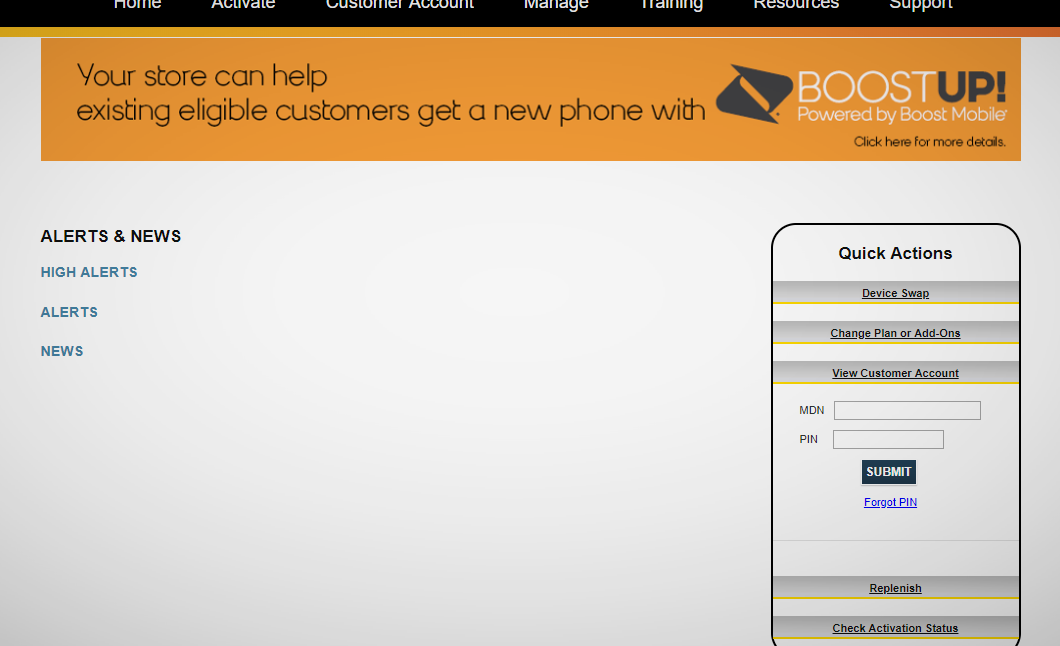
A screenshot shared with TechCrunch showed that anyone with access to this portal allowed the user to conduct a
device swap, change plans and add-ons, replenish a customer account, check activation status and view customer account information.
A
screenshot showing an internal customer portal.
All a user would need is a customer mobile phone number and a four-digit PIN number, which
could be bypassed by cycling through every possible combination.
The researcher said there were no limits on the number of PIN
attempts.
Account PIN numbers are highly sensitive as they can be used to transfer ownership from one person to another
That gives hackers an easier route to carry out a &SIM swapping& attack, which target and hijackcell phone numbers
Hackers use a mix of techniques — such as calling up customer service and impersonating a customer, all the way to recruiting telecom
employees to hijack SIM cards from the inside
In hijacking phone numbers, hackers can break into online accounts to steal vanity Instagram usernames, and intercept codes for two-factor
authentication to steal the contents of cryptocurrency wallets.
SIM swapping is becoming a big, albeit illegal business
An investigation by Motherboard revealed that hundreds of people across the US have had their cellphone number stolen over the past few
TechCrunch John Biggs was one such victim.
But the authorities are catching up to the growing threat of SIM swapping.Three SIM swappers have
been arrestedin the past few weeks alone.